World class IT services packed with enterprise technologies
Read the latest industry news and technical how-to's
Security SecurityComplianceSOC 2Managed Services
What Is SOC 2 Compliance? Complete SMB Guide (2026)
Cloud AWSAzureGCPNetworkingCloudInfrastructureSecurity
VLANs vs Subnets in Cloud: Which Do You Need?
Modern Workplace DevOpsManaged Services
How to Incorporate Agile Methodology in Your IT Organization

Infrastructure AWSAzureCloudData & AnalyticsInfrastructure
![Cloud Engineer Salary by City [2026 Data]](/uploads/hero-average-cloud-engineer-salary-by-city.webp)
![How to Build a Remote Engineering Team [2026]](/uploads/hero-building-remote-engineering-team.webp)
![Azure Landing Zones: Architecture Best Practices [2026]](/uploads/hero-azure-landing-zone-best-practices.webp)
![Azure Cost Management: Dashboard Setup Guide [2026]](/uploads/hero-azure-cost-management-dashboard-setup.webp)
![HIPAA Compliance Checklist for Cloud Apps [2026]](/uploads/hero-hipaa-compliance-checklist-cloud-healthcare.webp)

![Managed IT Services Pricing: What to Expect [2026]](/uploads/hero-managed-it-services-pricing-guide.webp)
![Microsoft 365 Security Hardening Checklist [2026]](/uploads/hero-microsoft-365-security-hardening-checklist.webp)
![Migrate Active Directory to Azure AD [Step-by-Step]](/uploads/hero-migrate-active-directory-to-azure-ad.webp)


![NIST 800-171 vs CMMC 2.0: Key Differences [2026]](/uploads/hero-nist-800-171-vs-cmmc-2-differences.webp)
![SOC 2 Audit Prep: 90-Day Checklist [Template]](/uploads/hero-soc-2-audit-preparation-90-day-checklist.webp)
![50+ DevOps Interview Questions [2026 Guide]](/uploads/hero-technical-interview-questions-devops.webp)
![N-1 Meaning in IT, Statistics & Science [Explained]](/uploads/hero-n-1-meaning-it-statistics-science.webp)
![Terraform vs Bicep vs ARM Templates [2026 Compared]](/uploads/hero-terraform-vs-bicep-vs-arm-templates.webp)
![Deploy Azure Virtual Desktop Step by Step [2026]](/uploads/2314800-AVD-BLOG-1.webp)














![N+1 vs 2N Redundancy Explained [2026 Guide]](/uploads/hero-what-does-n-1-mean-in-it.webp)


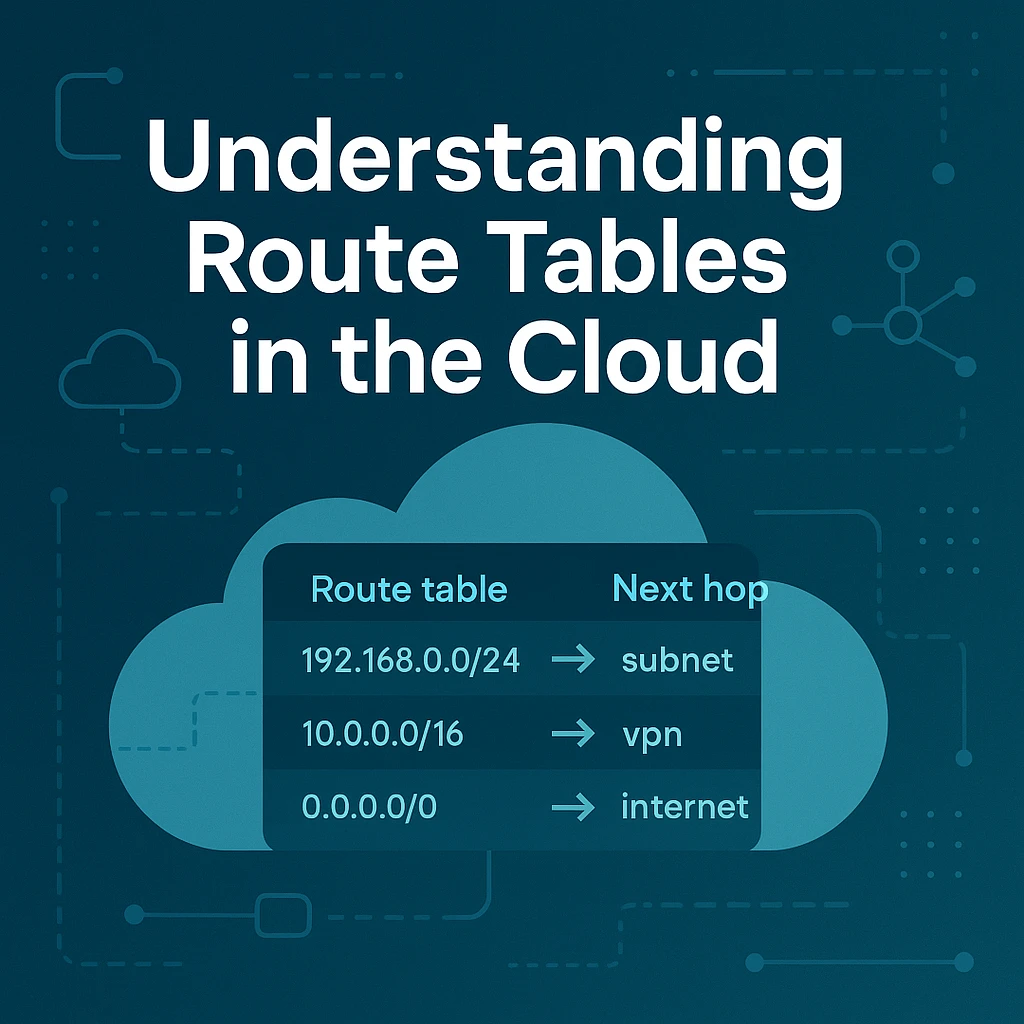

![Fix AD Replication Failures Fast [Proven Steps]](/uploads/ChatGPT-Image-Jun-27-2025-01_29_53-PM.webp)



![10 Azure Migration Mistakes to Avoid [2026]](/uploads/ChatGPT-Image-Jun-24-2025-10_32_01-AM.webp)

![Jumpbox vs Bastion Host vs Azure Bastion [2026]](/uploads/ChatGPT-Image-Jun-20-2025-12_18_01-PM.webp)
![How to Build a Tech Stack That Scales [2026]](/uploads/ChatGPT-Image-Jun-20-2025-03_16_34-PM.webp)

![Infrastructure as Code Explained [Beginner Guide]](/uploads/ChatGPT-Image-Jun-20-2025-01_21_59-PM.webp)
![Azure Key Vault Access Denied? Fix It Now [2026]](/uploads/ChatGPT-Image-Jun-18-2025-03_47_01-PM.webp)
![Azure Monitor Missing Metrics? 8 Fixes [2026]](/uploads/ChatGPT-Image-Jun-18-2025-04_04_10-PM.webp)
![Fix Azure SSO Issues: AADSTS Error Guide [2026]](/uploads/ChatGPT-Image-Jun-18-2025-03_18_28-PM.webp)





![Data Breach Costs for Small Business [2026 Data]](/uploads/Jasper_2025-01-31T203A373A34.163Z.webp)



![What Is DevOps? Complete Beginner's Guide [2026]](/uploads/60e68747-06b1-412b-ae83-ff9f120eb079.webp)

![How Kubernetes Actually Works [Visual Guide]](/uploads/f79db6d5-60ca-4939-8b5e-182f524dcdbf.webp)








![ChatGPT API Integration Guide [With Examples]](/uploads/photo-1626387753307-5a329fa44578.webp)

![NOC vs SOC: 7 Critical Differences [Compared]](/uploads/1_cLfFeIEJmoHA4wkPcwFgNA.webp)





![Build Azure Dashboards in Minutes [2026 Guide]](/uploads/photo-1599658880436-c61792e70672.webp)